
5 Steps to Prevent Insider Data Breaches
When you think about data leaks, what’s the first thing that comes to mind?Hackers? Trojans? Ransomware attacks? If your perception of organizational vulnerabilities (as they pertain to confidential data) is shaped by highly publicized, malicious, outside-in attacks, then you’re in the majority.But did you know that leaks triggered by internal players, tools and processes account for as many, if not more instances of debilitating breaches suffered by American organizations? Yet, with all the attention being hogged by hacking, hacktivism, DDoS and other forms of outside-in attacks, insider data breaches haven’t been receiving the attention they deserve.
This reflects in the security plans and policies of most organizations, which allocate a disproportionate share of their security budgets to preventing, mitigating and reacting to outside-in data breaches at the cost ignoring insider data threats.But to continue to ignore insider threats would be an egregious error. Just a few days ago, Gizmodo published an exposé that revealed that a marketing firm contracted by the Republican National Committee (RNC) unwittingly exposed the addresses, birthdates, phone numbers and a wealth of affiliation and profiling data of more than 198 million Americans, about 61% of the population. More than a terabyte of exposed data, which resided on an Amazon server remained accessible to the public for nearly two weeks before it was discovered by Chris Vickery, a cyber-risk analyst at UpGuard.To quote Vickery from a Business Insider article, "I find data breach situations like this all day long, every day. Companies don't realize their employees are cutting corners, and mistakes get made. It's an absolute epidemic."A few years ago, Court Ventures, a data broker owned by the credit monitoring agency Experian was tricked into exposing 200 million personal records, which included names, social security numbers, dates of birth and bank account numbers to a malicious actor posing as a private investigator.But for every RNC and Experian, there’re a thousand other leaks that occur from the inside each year that we never hear about. The irony of this situation is that nearly half of all organizations impacted by inside-out breaches take a month or longer to learn that they’ve suffered a breach! Take a look at this chart below from the Ponemon institute and Varonis.
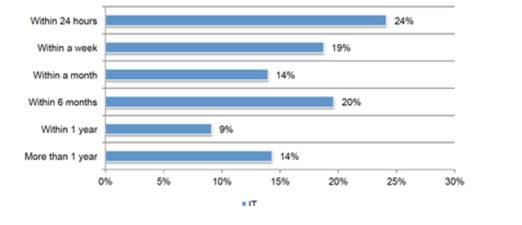
Source: Ponemon Institute/VaronisWhy and How do Breaches Occur From the Inside?Not surprisingly, many insider breaches aren’t triggered by malicious or activist intent. Oftentimes, it's a well-meaning but careless employee, contractor or partner, like in the case of the recent RNC breach that unwittingly exposes highly sensitive information.Because humans are innately fallible, organizations need better systems and processes to detect and mitigate insider leaks before it’s too late. But more on that in a moment.There are five scenarios that insider leaks most commonly occur in:1. Accidental Leaks - Internal players accidentally expose information without realizing that they have, as in the cases of the recent RNC breach, and a data breach at Google where a vendor accidentally shared personal information of an unspecified number of Google employees with another company.2. Emotional Actors - Disgruntled insiders aiming to disrupt or destabilize the organization, as with last year’s major submarine data leak where a disgruntled employee of the Indian government exposed 24,000 pages of classified information on India’s new Scorpene submarines.3. Opportunistic Insiders - Employees or contractors who steal an organization’s data to profit from it, as in the case of Flowers Hospital, where an employee stole patient information and used it to file fraudulent income tax returns.4. Compromised Insiders - Insiders whose identities or devices are compromised, and leveraged for profit, political or other reasons. A prominent (albeit dated) example being the leakage of 196,000 HP employees records from a laptop belonging to a Fidelity Investments employee.5. System and Configuration Glitches - Although less common, misconfigured, buggy or improperly deployed systems having access to sensitive data can cause leaks. A prominent example being the leakage of social security numbers belonging to nearly 2 million recipients of unemployment benefits after a software update on a computer belonging to the state of Michigan.How Can You Protect Your Organization From Insider Threats?Without further ado, here are five actions you can take immediately to beef up data security, and protect your organization from insider data breaches:1. Reevaluate your Security Policies and ProcessesChances are that you have fairly extensive policies, processes and tools for outside-in security, but not so much for inside-out security. If so, you need to act before your next leak occurs. Expand your security strategy to include comprehensive coverage for inside-out leakage risks. Think through scenarios that make your organization vulnerable on the inside, define best-practices and processes to mitigate them.2. Rebalance your Security BudgetAllocate a more balanced budget between outside-in and inside-out security tools and applications. Invest in solutions that protect your organization from the inside - think of them as your insurance policy for inside-out leaks. Select tools that will also keep you compliant with the regional and industry regulations that your organization is subject to.3. Identify and Classify your Sensitive DataThe first principle of inside-out security is - all data is not created equal. Have you identified the different types of sensitive data that your business deal with? Are you aware of which teams, individuals inside and outside your organization have access to sensitive data? Do you know where your sensitive business information resides? Because it’s incredibly hard to monitor every file every few minutes for sensitive content, you should invest in tools that will monitor your content repositories for you.4. Monitor and Control Access to Sensitive DataWhen you identify (not just once, but on an ongoing basis) where your sensitive data resides, the logical next step is to lock-down access to the data. Perform detailed and ongoing audits to continuously monitor access privileges for your sensitive data, and tune them to ensure that only authorized individuals have access. Deploy solutions that can restrict the movement of sensitive content outside your organization, as well as into the multitude of devices your employees use everyday.5. Restructure Your Content RepositoriesDo you have sensitive, regulated data residing in cloud or other third-party owned, multi-tenant infrastructure? Perhaps you have government contracts that prohibit you from storing data in infrastructure that isn't owned and managed by your organization. If so, how confident are you that your business is compliant? Once you’ve identified your regulated or contractually restricted data, consider moving it inside your firewall into dedicated infrastructure that you own and manage. Deploy a solution that can automatically detect and move regulated content to your on-premises repositories without disruption, ensuring that users have seamless access regardless of where the content resides.Want to learn more? Attend this 30 minute webinar to find out how you can better protect your organization on the inside!





